I’m running a WordPress instance on a Zimaboard on the home network. Normally, that’s the kind of thing I’d put on the paid hosting service so I can let someone else worry about patching the OS and such, but since family calendars and the like don’t need to be on the public internet, I decided to do this one in-house.
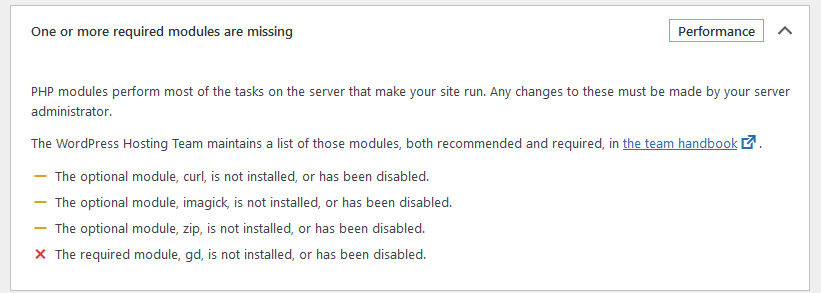
Once I got WordPress up and running, I checked the “Site Health” and along with some old themes that needed to be cleaned up, there was a notice of a critical issue, telling me that “One or more required modules are missing.”
Expanding the dropdown, I saw the list included curl, imagick, zip, and gd. I tried to be thorough when installing PHP, but evidently missed a few. No biggie. Here’s how to fix it.
This is all running on Ubuntu, so the first step is to update the list of available packages. Because you always do that first.
$ sudo apt update -yNext, install the missing packages. These are php modules, so the package to install is named “php-” and then the module name. (e.g. php-curl).
$ sudo apt install php-gd php-imagick php-curl php-zipMy machine is running PHP 8.1, so apt determined that the correct packages to install were php8.1-gd, php8.1-imagick, php8.1-curl, and php8.1-zip
Now I know the php-imagick module depends on ImageMagick, so I wanted to make sure that was installed, so after checking the apt command’s help text, I ran apt list -a ImageMagick
$ apt list -a ImageMagick
Listing... Done
imagemagick/jammy-updates,jammy-security,now 8:6.9.11.60+dfsg-1.3ubuntu0.22.04.3 amd64 [installed]
imagemagick/jammy 8:6.9.11.60+dfsg-1.3build2 amd64Excellent. Everything should be good now right? That’s what I thought, but WordPress disagreed. Returning the Site Health page, the same message appeared, telling me that “One or more required modules are missing.”
I had to scratch my head for a bit on that one. Then I remembered, you don’t just install PHP modules, you also have to tell PHP you want to use them. (For example, Xdebug notoriously causes programs to run more slowly.)
You use phpenmod to enable modules and phpdismod to disable them. (Arguably, I should have included “-s apache2” so they would only be enabled for Apache, but I wanted to make them available for any use of PHP.)
After enabling the modules, you also need to restart apache so the new modules are loaded, so the final set of commands is:
$ sudo phpenmod curl imagick zip gd
$ sudo systemctl restart apache2And now the Site Health report is a little bit happier.